Advanced penetration testing with kali linux pdf Big Trout Lake
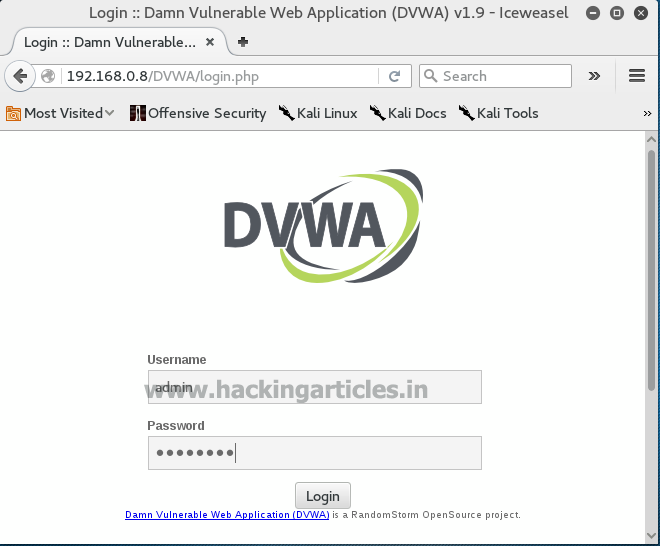
Advanced Penetration Testing With Kali Linux Penetration The institute provides a course on Kali Linux Which is an advanced penetration testing and Security auditing Linux distribution. There students will be able to install and configure Kali Linux and understand the penetration testing standards.
Advanced Penetration Testing Wiley Online Books
Advanced Penetration Testing cybrary.it. Advanced Penetration Testing goes beyond Kali linux and Metasploit and to provide you advanced pen testing for high security networks. Violent Python Author : TJ O'Connor, What about Kali Linux • Formerly Known as Backtrack • Linux Distribution exclusively for Security Testing developed by Mati Aharoni and Devon Kearns of.
Build a better defense against motivated, organized, professional attacks. Advanced Penetration Testing: Hacking the World’s Most Secure Networks takes hacking far beyond Kali linux and Metasploit to provide a more complex attack simulation. What about Kali Linux • Formerly Known as Backtrack • Linux Distribution exclusively for Security Testing developed by Mati Aharoni and Devon Kearns of
Download or Read Book Master the art of exploiting advanced web penetration techniques with Kali Linux 2016.2 About This Book Make the most out of advanced web pen-testing techniques using Kali Linux 2016.2 Explore how Stored (a.k.a. Persistent) XSS attacks work and how to take advantage of them Learn to secure your application by performing Book Description. This book will make you an expert in Kali Linux penetration testing. It covers all the most advanced tools and techniques to reproduce the methods used by sophisticated hackers.
What about Kali Linux • Formerly Known as Backtrack • Linux Distribution exclusively for Security Testing developed by Mati Aharoni and Devon Kearns of Advanced Penetration Testing goes beyond Kali linux and Metasploit and to provide you advanced pen testing for high security networks. Violent Python Author : TJ O'Connor
What about Kali Linux • Formerly Known as Backtrack • Linux Distribution exclusively for Security Testing developed by Mati Aharoni and Devon Kearns of Build a better defense against motivated, organized, professional attacks. Advanced Penetration Testing: Hacking the World’s Most Secure Networks takes hacking far beyond Kali linux and Metasploit to provide a more complex attack simulation.
Advanced Penetration Testing goes beyond Kali linux and Metasploit and to provide you advanced pen testing for high security networks. Table of Contents 1: Medical Records (In)security Kali Linux is the pen-testing professional's main tool, and includes many hundreds of modules for scanning, exploitation, payloads, and post exploitation. In this course you can learn how to use Kali for advanced pen testing, including stealthy testing, privilege escalation, tunneling and exfiltration, and pivoting. Learn how to use the basic toolset and extend Kali, integrating native
The institute provides a course on Kali Linux Which is an advanced penetration testing and Security auditing Linux distribution. There students will be able to install and configure Kali Linux and understand the penetration testing standards. Kali Linux 2 is the most advanced and feature rich penetration testing platform available. This hands-on learn by doing book will help take you beyond the basic features of Kali into a more advanced understanding of the tools and techniques used in security testing. If you have a basic understanding
About This Book Employ advanced pentesting techniques with Kali Linux to build highly-secured systems Get to grips with various stealth techniques to remain undetected and defeat the latest defenses and follow proven approaches Select and configure the most effective tools from Kali Linux to test network security and prepare your business against malicious threats and save costs Who This … Advanced Penetration. Testing With Kali Linux Lecture 1 : Introduction What is Penetration Testing • Offence for Defence • White hat hackers do it for security.
20/09/2017 · Penetration Testers, IT professional or a security consultant who wants to maximize the success of your network testing using some of the advanced features of Kali Linux… What about Kali Linux • Formerly Known as Backtrack • Linux Distribution exclusively for Security Testing developed by Mati Aharoni and Devon Kearns of
About This Book Employ advanced pentesting techniques with Kali Linux to build highly-secured systems Get to grips with various stealth techniques to remain undetected and defeat the latest defenses and follow proven approaches Select and configure the most effective tools from Kali Linux to test network security and prepare your business against malicious threats and save costs Who This … About This Book Employ advanced pentesting techniques with Kali Linux to build highly-secured systems Get to grips with various stealth techniques to remain undetected and defeat the latest defenses and follow proven approaches Select and configure the most effective tools from Kali Linux to test network security and prepare your business against malicious threats and save costs Who This …
The institute provides a course on Kali Linux Which is an advanced penetration testing and Security auditing Linux distribution. There students will be able to install and configure Kali Linux and understand the penetration testing standards. Mastering Kali Linux for Advanced Penetration Testing Download PDF (9 MB) A practical guide to testing your network's security with Kali Linux - the preferred choice of penetration …
Advanced Penetration Testing Wiley Online Books
Penetration Testing Advanced Kali Linux linkedin.com. 20/09/2017 · Penetration Testers, IT professional or a security consultant who wants to maximize the success of your network testing using some of the advanced features of Kali Linux…, The institute provides a course on Kali Linux Which is an advanced penetration testing and Security auditing Linux distribution. There students will be able to install and configure Kali Linux and understand the penetration testing standards..
Advanced Penetration Testing Wiley Online Books
Advanced Penetration Testing cybrary.it. The institute provides a course on Kali Linux Which is an advanced penetration testing and Security auditing Linux distribution. There students will be able to install and configure Kali Linux and understand the penetration testing standards. About This Book Employ advanced pentesting techniques with Kali Linux to build highly-secured systems Get to grips with various stealth techniques to remain undetected and defeat the latest defenses and follow proven approaches Select and configure the most effective tools from Kali Linux to test network security and prepare your business against malicious threats and save costs Who This ….
Ebook Description. This book provides an overview of the kill chain approach to penetration testing, and then focuses on using Kali Linux to provide examples of how this methodology is … Advanced Penetration Testing With Kali Linux v2.0 Introduction to kali Linux Installing Kali Linux Configure Network Connection Administering Kali Linux Updating and Upgrading kali Linux
About This Book Employ advanced pentesting techniques with Kali Linux to build highly-secured systems Get to grips with various stealth techniques to remain undetected and defeat the latest defenses and follow proven approaches Select and configure the most effective tools from Kali Linux to test network security and prepare your business against malicious threats and save costs Who This … Build a better defense against motivated, organized, professional attacks. Advanced Penetration Testing: Hacking the World’s Most Secure Networks takes hacking far beyond Kali linux and Metasploit to provide a more complex attack simulation.
Advanced Penetration Testing goes beyond Kali linux and Metasploit and to provide you advanced pen testing for high security networks. Violent Python Author : TJ O'Connor Ebook Description. This book provides an overview of the kill chain approach to penetration testing, and then focuses on using Kali Linux to provide examples of how this methodology is …
Advanced Penetration Testing goes beyond Kali linux and Metasploit and to provide you advanced pen testing for high security networks. Table of Contents 1: Medical Records (In)security Build a better defense against motivated, organized, professional attacks. Advanced Penetration Testing: Hacking the World’s Most Secure Networks takes hacking far beyond Kali linux and Metasploit to provide a more complex attack simulation.
Mastering Kali Linux for Advanced Penetration Testing Download PDF (9 MB) A practical guide to testing your network's security with Kali Linux - the preferred choice of penetration … Advanced Penetration Testing goes beyond Kali linux and Metasploit and to provide you advanced pen testing for high security networks. Table of Contents 1: Medical Records (In)security
About This Book Employ advanced pentesting techniques with Kali Linux to build highly-secured systems Get to grips with various stealth techniques to remain undetected and defeat the latest defenses and follow proven approaches Select and configure the most effective tools from Kali Linux to test network security and prepare your business against malicious threats and save costs Who This … Book Description. This book will make you an expert in Kali Linux penetration testing. It covers all the most advanced tools and techniques to reproduce the methods used by sophisticated hackers.
Advanced Penetration Testing goes beyond Kali linux and Metasploit and to provide you advanced pen testing for high security networks. Violent Python Author : TJ O'Connor Ebook Description. This book provides an overview of the kill chain approach to penetration testing, and then focuses on using Kali Linux to provide examples of how this methodology is …
Advance penetration testing with Kali Linux Introduction to kali Linux What is new in kali linux Installing kali linux Configure Network Connection Using kali Linux Update kali Linux Penetration Testing Standard Open Web Application Security Project (OWASP) Licensee Penetration Testing (LPT) Penetration Testing Classification White Box and Black Box Penetration Testing vs … Kali Linux is the pen-testing professional's main tool, and includes many hundreds of modules for scanning, exploitation, payloads, and post exploitation. In this course you can learn how to use Kali for advanced pen testing, including stealthy testing, privilege escalation, tunneling and exfiltration, and pivoting. Learn how to use the basic toolset and extend Kali, integrating native
About This Book Employ advanced pentesting techniques with Kali Linux to build highly-secured systems Get to grips with various stealth techniques to remain undetected and defeat the latest defenses and follow proven approaches Select and configure the most effective tools from Kali Linux to test network security and prepare your business against malicious threats and save costs Who This … Kali Linux 2 is the most advanced and feature rich penetration testing platform available. This hands-on learn by doing book will help take you beyond the basic features of Kali into a more advanced understanding of the tools and techniques used in security testing. If you have a basic understanding
Kali Linux is the pen-testing professional's main tool, and includes many hundreds of modules for scanning, exploitation, payloads, and post exploitation. In this course you can learn how to use Kali for advanced pen testing, including stealthy testing, privilege escalation, tunneling and exfiltration, and pivoting. Learn how to use the basic toolset and extend Kali, integrating native About This Book Employ advanced pentesting techniques with Kali Linux to build highly-secured systems Get to grips with various stealth techniques to remain undetected and defeat the latest defenses and follow proven approaches Select and configure the most effective tools from Kali Linux to test network security and prepare your business against malicious threats and save costs Who This …
Advanced Penetration Testing: Hacking the World's Most Secure Networks takes hacking far beyond Kali linux and Metasploit to provide a more complex attack simulation. Featuring techniques not taught in any certification prep or covered by common defensive scanners, this book integrates social Advanced Penetration Testing With Kali Linux v2.0 Introduction to kali Linux Installing Kali Linux Configure Network Connection Administering Kali Linux Updating and Upgrading kali Linux
View and Download Bose SOUNDLINK COLOR II owner's manual online. SOUNDLINK COLOR II Speakers pdf manual download. Bose soundlink colour manual pdf Georgian Sands Beach Midnight Blue Protective Case for Bose SoundLink Micro Bluetooth Speaker, Best Color and Shape Matching, Featured Secure and Easy Pulling Out Strap Design, Mesh Pocket for Cable and accessorie 4.6 out of 5 stars 36
Advanced Penetration Testing With Kali Linux

Advanced Penetration Testing Wiley Online Books. Advance penetration testing with Kali Linux Introduction to kali Linux What is new in kali linux Installing kali linux Configure Network Connection Using kali Linux Update kali Linux Penetration Testing Standard Open Web Application Security Project (OWASP) Licensee Penetration Testing (LPT) Penetration Testing Classification White Box and Black Box Penetration Testing vs …, The institute provides a course on Kali Linux Which is an advanced penetration testing and Security auditing Linux distribution. There students will be able to install and configure Kali Linux and understand the penetration testing standards..
Advanced Penetration Testing With Kali Linux
Advanced Penetration Testing With Kali Linux v2. Advanced Penetration Testing: Hacking the World's Most Secure Networks takes hacking far beyond Kali linux and Metasploit to provide a more complex attack simulation. Featuring techniques not taught in any certification prep or covered by common defensive scanners, this book integrates social, Ebook Description. This book provides an overview of the kill chain approach to penetration testing, and then focuses on using Kali Linux to provide examples of how this methodology is ….
Download or Read Book Master the art of exploiting advanced web penetration techniques with Kali Linux 2016.2 About This Book Make the most out of advanced web pen-testing techniques using Kali Linux 2016.2 Explore how Stored (a.k.a. Persistent) XSS attacks work and how to take advantage of them Learn to secure your application by performing Download or Read Book Master the art of exploiting advanced web penetration techniques with Kali Linux 2016.2 About This Book Make the most out of advanced web pen-testing techniques using Kali Linux 2016.2 Explore how Stored (a.k.a. Persistent) XSS attacks work and how to take advantage of them Learn to secure your application by performing
What about Kali Linux • Formerly Known as Backtrack • Linux Distribution exclusively for Security Testing developed by Mati Aharoni and Devon Kearns of 20/09/2017 · Penetration Testers, IT professional or a security consultant who wants to maximize the success of your network testing using some of the advanced features of Kali Linux…
Download or Read Book Master the art of exploiting advanced web penetration techniques with Kali Linux 2016.2 About This Book Make the most out of advanced web pen-testing techniques using Kali Linux 2016.2 Explore how Stored (a.k.a. Persistent) XSS attacks work and how to take advantage of them Learn to secure your application by performing About This Book Employ advanced pentesting techniques with Kali Linux to build highly-secured systems Get to grips with various stealth techniques to remain undetected and defeat the latest defenses and follow proven approaches Select and configure the most effective tools from Kali Linux to test network security and prepare your business against malicious threats and save costs Who This …
Advance penetration testing with Kali Linux Introduction to kali Linux What is new in kali linux Installing kali linux Configure Network Connection Using kali Linux Update kali Linux Penetration Testing Standard Open Web Application Security Project (OWASP) Licensee Penetration Testing (LPT) Penetration Testing Classification White Box and Black Box Penetration Testing vs … What about Kali Linux • Formerly Known as Backtrack • Linux Distribution exclusively for Security Testing developed by Mati Aharoni and Devon Kearns of
Advanced Penetration Testing With Kali Linux v2.0 Introduction to kali Linux Installing Kali Linux Configure Network Connection Administering Kali Linux Updating and Upgrading kali Linux Advanced Penetration Testing goes beyond Kali linux and Metasploit and to provide you advanced pen testing for high security networks. Table of Contents 1: Medical Records (In)security
Advanced Penetration Testing goes beyond Kali linux and Metasploit and to provide you advanced pen testing for high security networks. Table of Contents 1: Medical Records (In)security Book Description. This book will make you an expert in Kali Linux penetration testing. It covers all the most advanced tools and techniques to reproduce the methods used by sophisticated hackers.
Kali Linux 2 is the most advanced and feature rich penetration testing platform available. This hands-on learn by doing book will help take you beyond the basic features of Kali into a more advanced understanding of the tools and techniques used in security testing. If you have a basic understanding Mastering Kali Linux for Advanced Penetration Testing Download PDF (9 MB) A practical guide to testing your network's security with Kali Linux - the preferred choice of penetration …
Kali Linux 2 is the most advanced and feature rich penetration testing platform available. This hands-on learn by doing book will help take you beyond the basic features of Kali into a more advanced understanding of the tools and techniques used in security testing. If you have a basic understanding Advanced Penetration Testing: Hacking the World's Most Secure Networks takes hacking far beyond Kali linux and Metasploit to provide a more complex attack simulation. Featuring techniques not taught in any certification prep or covered by common defensive scanners, this book integrates social
About This Book Employ advanced pentesting techniques with Kali Linux to build highly-secured systems Get to grips with various stealth techniques to remain undetected and defeat the latest defenses and follow proven approaches Select and configure the most effective tools from Kali Linux to test network security and prepare your business against malicious threats and save costs Who This … Ebook Description. This book provides an overview of the kill chain approach to penetration testing, and then focuses on using Kali Linux to provide examples of how this methodology is …
What about Kali Linux • Formerly Known as Backtrack • Linux Distribution exclusively for Security Testing developed by Mati Aharoni and Devon Kearns of Advanced Penetration Testing goes beyond Kali linux and Metasploit and to provide you advanced pen testing for high security networks. Yo Will Also Like: Cybersecurity Incident Response Book Free Pdf
Advanced Penetration Testing Hacking the World's Most

Advanced Penetration Testing Hacking the World’s Most. Book Description. This book will make you an expert in Kali Linux penetration testing. It covers all the most advanced tools and techniques to reproduce the methods used by sophisticated hackers., About This Book Employ advanced pentesting techniques with Kali Linux to build highly-secured systems Get to grips with various stealth techniques to remain undetected and defeat the latest defenses and follow proven approaches Select and configure the most effective tools from Kali Linux to test network security and prepare your business against malicious threats and save costs Who This ….
Penetration Testing Advanced Kali Linux linkedin.com

Advanced Penetration Testing Hacking the World’s Most. Advanced Penetration Testing: Hacking the World's Most Secure Networks takes hacking far beyond Kali linux and Metasploit to provide a more complex attack simulation. Featuring techniques not taught in any certification prep or covered by common defensive scanners, this book integrates social Advanced Penetration Testing: Hacking the World's Most Secure Networks takes hacking far beyond Kali linux and Metasploit to provide a more complex attack simulation. Featuring techniques not taught in any certification prep or covered by common defensive scanners, this book integrates social.

Advanced Penetration Testing goes beyond Kali linux and Metasploit and to provide you advanced pen testing for high security networks. Author Bios Wil Allsopp is an IT security expert with 20 years experience, specializing in red team engagements, penetration testing, vulnerability assessment, security audits, secure source code review, social engineering, and advanced persistent threats. About This Book Employ advanced pentesting techniques with Kali Linux to build highly-secured systems Get to grips with various stealth techniques to remain undetected and defeat the latest defenses and follow proven approaches Select and configure the most effective tools from Kali Linux to test network security and prepare your business against malicious threats and save costs Who This …
Ebook Description. This book provides an overview of the kill chain approach to penetration testing, and then focuses on using Kali Linux to provide examples of how this methodology is … The institute provides a course on Kali Linux Which is an advanced penetration testing and Security auditing Linux distribution. There students will be able to install and configure Kali Linux and understand the penetration testing standards.
About This Book Employ advanced pentesting techniques with Kali Linux to build highly-secured systems Get to grips with various stealth techniques to remain undetected and defeat the latest defenses and follow proven approaches Select and configure the most effective tools from Kali Linux to test network security and prepare your business against malicious threats and save costs Who This … Advanced Penetration Testing goes beyond Kali linux and Metasploit and to provide you advanced pen testing for high security networks. Table of Contents 1: Medical Records (In)security
Book Description. This book will make you an expert in Kali Linux penetration testing. It covers all the most advanced tools and techniques to reproduce the methods used by sophisticated hackers. Build a better defense against motivated, organized, professional attacks. Advanced Penetration Testing: Hacking the World’s Most Secure Networks takes hacking far beyond Kali linux and Metasploit to provide a more complex attack simulation.
Advanced Penetration. Testing With Kali Linux Lecture 1 : Introduction What is Penetration Testing • Offence for Defence • White hat hackers do it for security. About This Book Employ advanced pentesting techniques with Kali Linux to build highly-secured systems Get to grips with various stealth techniques to remain undetected and defeat the latest defenses and follow proven approaches Select and configure the most effective tools from Kali Linux to test network security and prepare your business against malicious threats and save costs Who This …
The institute provides a course on Kali Linux Which is an advanced penetration testing and Security auditing Linux distribution. There students will be able to install and configure Kali Linux and understand the penetration testing standards. Advanced Penetration Testing: Hacking the World's Most Secure Networks takes hacking far beyond Kali linux and Metasploit to provide a more complex attack simulation. Featuring techniques not taught in any certification prep or covered by common defensive scanners, this book integrates social
Mastering Kali Linux for Advanced Penetration Testing Download PDF (9 MB) A practical guide to testing your network's security with Kali Linux - the preferred choice of penetration … Kali Linux is the pen-testing professional's main tool, and includes many hundreds of modules for scanning, exploitation, payloads, and post exploitation. In this course you can learn how to use Kali for advanced pen testing, including stealthy testing, privilege escalation, tunneling and exfiltration, and pivoting. Learn how to use the basic toolset and extend Kali, integrating native
Kali Linux is the pen-testing professional's main tool, and includes many hundreds of modules for scanning, exploitation, payloads, and post exploitation. In this course you can learn how to use Kali for advanced pen testing, including stealthy testing, privilege escalation, tunneling and exfiltration, and pivoting. Learn how to use the basic toolset and extend Kali, integrating native Book Description. This book will make you an expert in Kali Linux penetration testing. It covers all the most advanced tools and techniques to reproduce the methods used by sophisticated hackers.
Advanced Penetration Testing goes beyond Kali linux and Metasploit and to provide you advanced pen testing for high security networks. Table of Contents 1: Medical Records (In)security Mastering Kali Linux for Advanced Penetration Testing Download PDF (9 MB) A practical guide to testing your network's security with Kali Linux - the preferred choice of penetration …
Advance penetration testing with Kali Linux Introduction to kali Linux What is new in kali linux Installing kali linux Configure Network Connection Using kali Linux Update kali Linux Penetration Testing Standard Open Web Application Security Project (OWASP) Licensee Penetration Testing (LPT) Penetration Testing Classification White Box and Black Box Penetration Testing vs … Advanced Penetration Testing goes beyond Kali linux and Metasploit and to provide you advanced pen testing for high security networks. Table of Contents 1: Medical Records (In)security
Advanced Penetration Testing goes beyond Kali linux and Metasploit and to provide you advanced pen testing for high security networks. Yo Will Also Like: Cybersecurity Incident Response Book Free Pdf Download or Read Book Master the art of exploiting advanced web penetration techniques with Kali Linux 2016.2 About This Book Make the most out of advanced web pen-testing techniques using Kali Linux 2016.2 Explore how Stored (a.k.a. Persistent) XSS attacks work and how to take advantage of them Learn to secure your application by performing


